Understanding and Mitigating Cybersecurity Supply Chain Risks
Updated: June 24, 2023, to include information about the MOVEit vulnerability.
Protecting your company from cyber threats is hard enough — so why worry about anyone else? Because of supply chains. Because of Tier 1, Tier 2, and Tier 3 suppliers. Because you hire consultants and they hire subcontractors, every one of them is a potential vulnerability.
In cybersecurity, your business is only as safe as the systems it’s linked to. In a global digital environment, that can be dozens or hundreds of companies worldwide. Do you need to know about them?
Definitely.
To be sure, the concept of infinitely-expanding cybersecurity isn’t unique to supply chains. For instance, Attack Surface Management is about understanding how new vulnerabilities constantly pop up throughout your enterprise.
When defending your supply chain, you have a whole different set of risks and variables. You can’t control how your suppliers approach cybersecurity (though at times, and in certain situations, you might be able to influence them). But you need to understand it. Just because you don’t have control doesn’t mean you’re exempt from responsibility.
So how should you think about cybersecurity supply chain risk?
Let’s dive in.
Supply chain risk in cybersecurity starts with software
Companies are connected through Software-as-a-Service (SaaS) in the digital business world. As data flows between systems, it gains more exposure to cyber criminals.
If you’re a small business owner, you must consider every part of your digital supply chain in your cybersecurity defense plan. No matter how physically distant a supplier seems, they might as well be operating next door in terms of cyber risk.
Before the internet, this wasn’t as much of an issue. Materials were sourced more locally and regionally. Tier 3 suppliers could be overseas, but everyone’s systems were disparate. Company data didn’t pass through suppliers’ systems, as that was expensive and onerous.
As a result, cybersecurity wasn’t nearly as needed, so companies rarely prioritized it, let alone practiced it. Breaches were infrequent and typically facilitated by an insider, as that was the only viable way they could occur — OR by Tom Cruise, in a Mission: Impossible scenario (we have to admit, those were some great flicks!).
Times sure were simpler before the Internet.
Nowadays, everything’s connected, so a risk to one link in your supply chain is a potential risk to you. You may feel removed from the enterprise that produces the raw materials that make it into your product. But a cyber threat lurking in their systems (connect to yours) may be closer and more prevalent than you think.
Cybersecurity in an interconnected world: The 2023 MOVEit attack
New cyberattacks make global headlines daily, but some stand out above all others. The MOVEit attack grabbed the media’s attention, similar to the SolarWinds attack a few years before. Both are regrettable and upsetting incidents, but it’s important they become big stories so more people become aware of the need for new approaches to cybersecurity. More so, both attacks are prime examples of how no one can ever be 100% safe indefinitely in our interconnected world.
The United States public became generally aware of the MOVEit attack on June 7, 2023, when CISA — the Cybersecurity & Infrastructure Security Agency of the federal government — posted a press release with the headline: “#StopRansomware: CL0P Ransomware Gang Exploits CVE-2023-34362 MOVEit Vulnerability.” Here’s what they reported happened:
According to open source information, beginning on May 27, 2023, CL0P Ransomware Gang, also known as TA505, began exploiting a previously unknown SQL injection vulnerability (CVE-2023-34362) in Progress Software's managed file transfer (MFT) solution known as MOVEit Transfer. Internet-facing MOVEit Transfer web applications were infected with a web shell named LEMURLOOT, which was then used to steal data from underlying MOVEit Transfer databases. In similar spates of activity, TA505 conducted zero-day-exploit-driven campaigns against Accellion File Transfer Appliance (FTA) devices in 2020 and 2021, and Fortra/Linoma GoAnywhere MFT servers in early 2023.



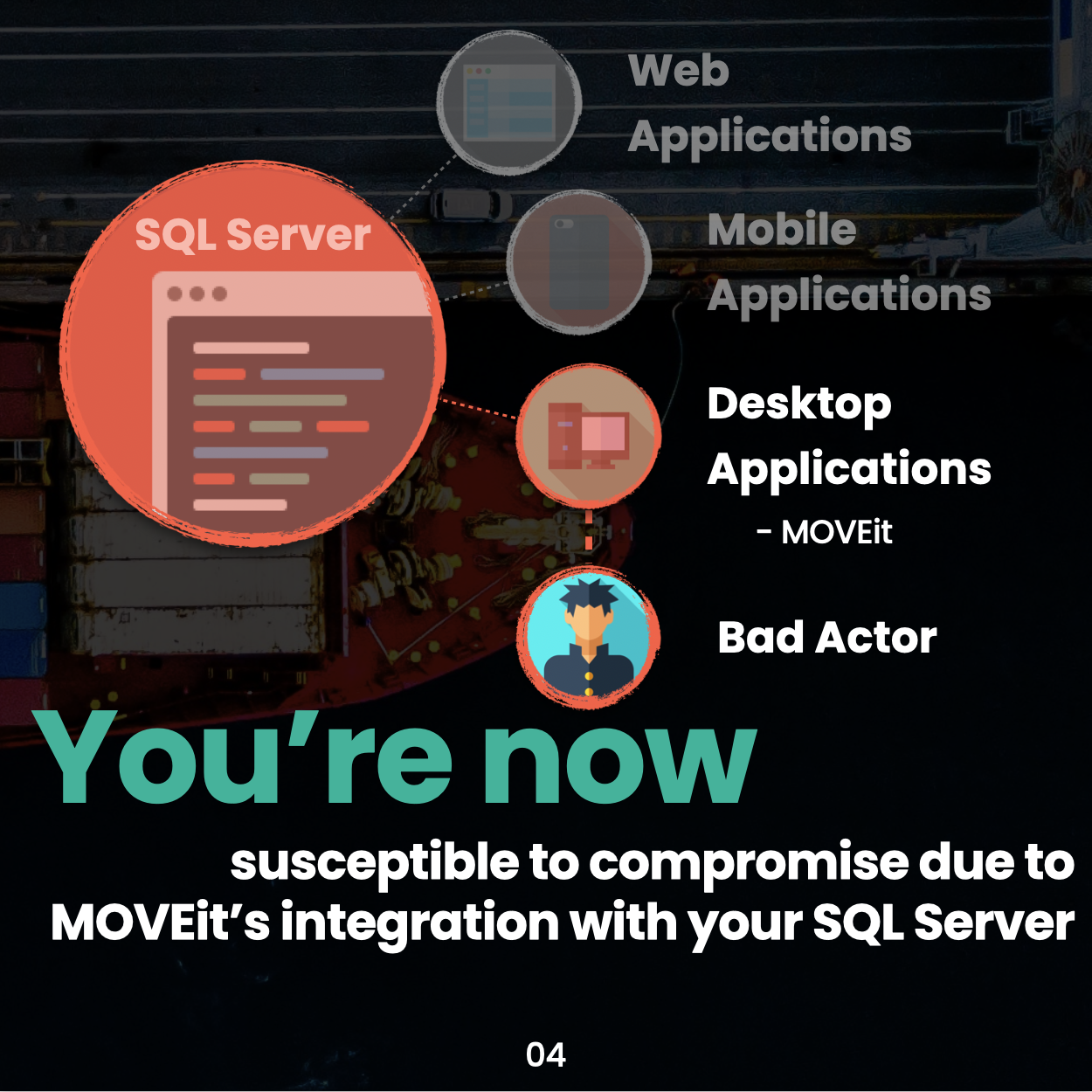
Let’s break that down in decodingCyber terms:
A cybercriminal group found a vulnerability in a common online file transfer system (MOVEit, owned by Progress Software) and took advantage of it to steal data. They have also conducted similar operations in 2020, 2021, and 2023, targeting another company, Accellion’s [rebranded as Kiteworks] file transfer software.
The press release includes plenty of technical information to help security teams assess their vulnerabilities. Then, it gives tips for mitigating these types of attacks. Some are meant for IT professionals, but others are ones that everyone should know and practice, including:
Implementing a data recovery plan
Maintaining offline data backups
Adhering to password best practices
Keeping software up to date
When a cyberattack becomes a household name, many organizations scramble to patch their systems, holding their breath as they determine whether they’ve finally run out of luck. But imagine this: You did everything right, but one of the dozens of companies you’re connected to didn’t. Could your data still be at risk? In an interconnected world, the harsh reality is that you’re only as safe as the least secure company you do business with.
A cyberattack rarely involves a single instance. The MOVEit attack has roots in previous exploits, and the perpetrators may continue their attacks until doing so stops being profitable. While, as of this writing, the victim count is still unknown, experts say it will be “at least hundreds, if not more” than currently known.
Different countries have different cybersecurity laws
Where this really matters for cybersecurity is in international business. If you buy supplies from a company in a different country, what are its cybersecurity laws and protections? Who has access to the data? Your supply chain could include organizations beholden to cybersecurity laws that significantly differ from the country where you are incorporated or do most of your business.
When you begin a relationship with a supplier, your first thought might be, “How much does this cost?” If the answer is “Not much,” and it seems reliable, you might sign a contract without due diligence.
Wait! Before doing anything too hasty, consider the potential complications when buying supplies from global suppliers.
Who are their suppliers’ suppliers? Where are their systems? What do they do for cybersecurity? Software allows us to seamlessly and quickly cross borders for business, and that can create the illusion of shared security. The reality can be different.
Could your data be seized, frozen, surveyed, or deleted just because it passes through another country? As a business owner, you want to answer this question in as much detail as possible. At the very least, you want to think about the risk.
Why your cloud provider matters for your supply chain
Many companies today put their data in the cloud. In doing so, you lose some level of control over your data but compared to keeping information on-premises, you gain speed and efficiency and tap into the logistics of the modern supply chain.
If your business is in the cloud, it probably depends on another company’s cloud infrastructure. Overall, this is good for your cybersecurity. Instead of having to do cybersecurity yourself, your cloud provider carries much (but not all) of the load for you. The administration of your network still falls to you, the tenant owner.
Bear in mind when you deploy your network/data to the cloud, you’re relying on another enterprise to be operational and secure. Said cloud provider is not part of your supply chain. That dependency means you must know how the data on their cloud is managed.
Here’s why this matters.
Let’s imagine your cloud provider is hit with a cyberattack. The incident might even impact your customers directly. That can’t be good.
However, an outside agency conducts an analysis and determines that your cloud provider is at fault. Whew! You didn’t do anything wrong, so everything is fine, right?
Not necessarily.
Think about your customers. Their data may have been compromised. Did they know you passed their data onto another company?
Let’s assume they did know (or do now). Are they going to complain to your cloud provider?
Probably not. Instead, they’ll ask you why you entrusted their data to a company that didn’t protect it.
They will want to know what you — not your cloud provider — are doing to resolve the situation. And if they decide to end a business relationship with anyone, it will not be with your cloud provider. It’s going to be with you.
2 essential cybersecurity questions to ask your cloud provider (or read about in the EULA … fun)
When you choose a cloud provider, here are some questions you want to be thinking about:
“What cybersecurity measures are you providing me at my level of service?”
While you may not have the opportunity (or need) to talk to their engineers about firewalls, you should at least get a clear understanding of how they’re protecting your data. You also want to know where that data lives physically.
“What are your notification processes in the event of a breach?”
Major cyber events have a history of being initially unreported. Sometimes the bad actors are inside systems undetected for months (or years). Other times the breached organization knows but doesn’t want to tell.
Pro-Tip
Aside from mandatory reporting, the optimal response is to share information with competitors, industry partners, and the government (particularly federal law enforcement). This level of responsibility and transparency strengthens the business community and helps protect against future threats.
In any case, you might be required, by law, to report the breach (or the cloud provider might, based on the law) depending on where you are located, where you do business, or where your customers reside.
Wrapping up our discussion on the supply chain threat
Overall, your cloud provider is part of the complex and interconnected systems that comprise the modern supply chain. To minimize those cyber risks, you need to gain as much visibility as possible into your supply chain and understand where it could be vulnerable — and what you can do to help.
Ready for more epic articles?
You had me at “hello.” Now, let’s share this heck out of this article!
Are you looking to go to a persona page?
Cyber 101 | The Solopreneur | SMB | BoD












