Small and Midsize Businesses (SMBs)
You’ve got a startup, own a mom & pop, or run a small company. We’ve got your cybersecurity covered.
WELCOME!
Cyber insights for organizational leaders
It doesn’t matter if you’re a…
Whether you’ve been open for two days or 20 years, your SMB (2-249 employees) needs to be safe and secure — and that starts with a solid understanding of cybersecurity.
COMMENCE LEARNING IN 3…2…1
Making learning easy is our jam!
Your learning journey begins here. We built this site to be easy to use and understand. Start with the first section, continue to the next, and enjoy the journey! Feel free to reach out to us if you have questions along the way.
Cheers!
ATTACK CLI, an original concept
SECTION ONE
CLI STANDS FOR Complexity, Likelihood, & Impact. You might wonder, “But wait, do I have to worry about cybersecurity? I’m a regular, lucrative law firm with 1000s of happy clients.” Yes!
ATTACK CLI FOR SMBs
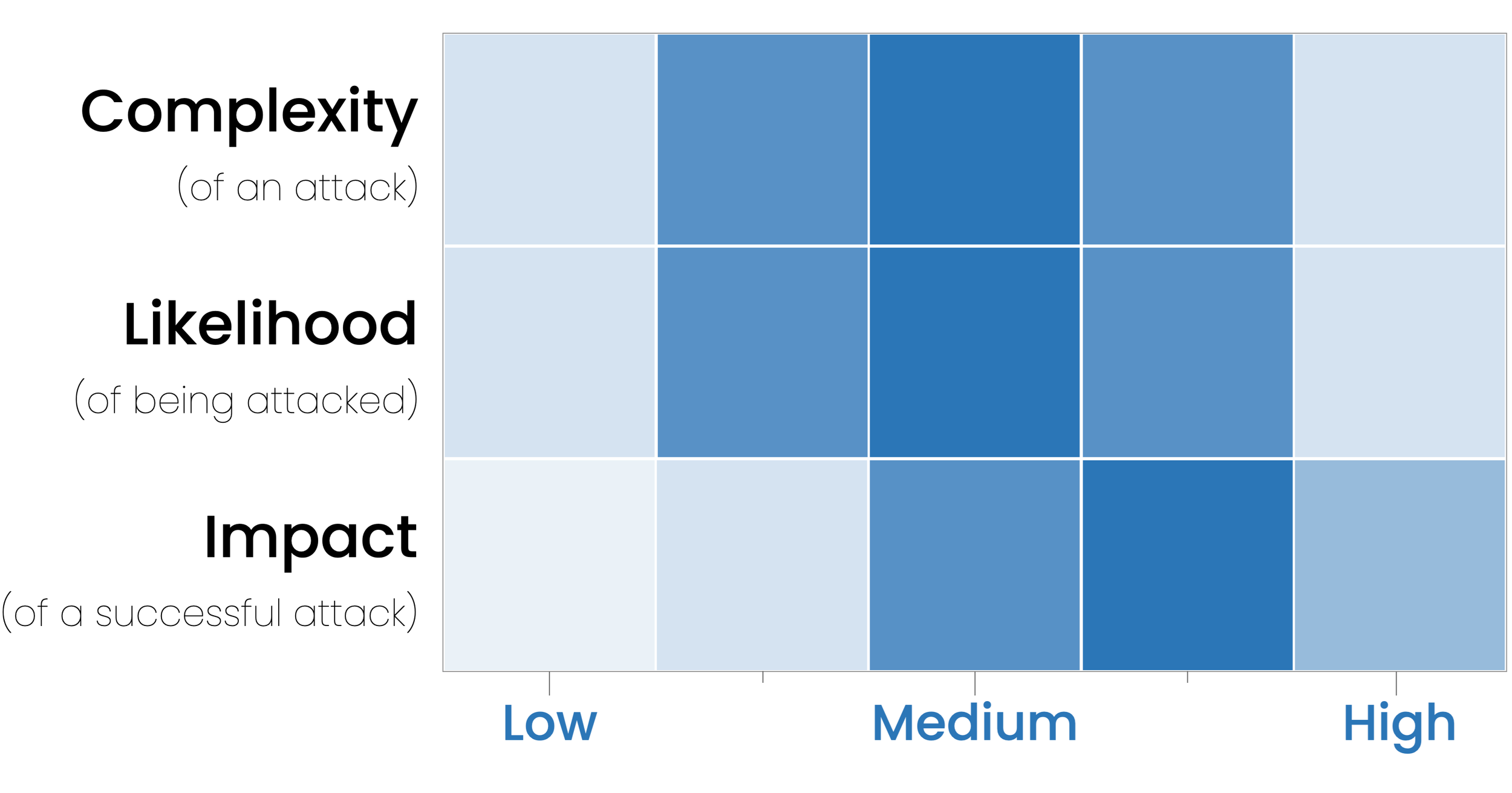
What is the Attack CLI? A snapshot showing the complexity of a cyber attack, the likelihood of being attacked, and the impact of a successful attack. They are all leveled based on the attack parameter they represent and placed in the heatmap you see above.
How should I think about my Attack CLI? As a guide, not an exact representation of your unique circumstances. Most SMBs will deal with MEDIUM COMPLEXITY attacks (from phishing to data breaches). They will have a MEDIUM LIKELIHOOD of being attacked (not terrible). However, most SMBs will suffer a MEDIUM+ IMPACT from a successful attack (if you are prepared for the threat, the impact could be low, but if you aren't, the impact could be substantial).
Why is the Attack CLI for SMBs primarily anchored to "medium?” Your company isn’t just a personal blog connected to a bank account—but it’s not a global financial institution with thousands of employees and millions of customers either.
Curious about how to approach cybersecurity? SMBs must balance security and usability. You need to address concerns and mitigate risk, but you also want to make business easy for your customers. Bear in mind that bad actors consider data as valuable as cash. If you have data, you have something of value to a bad actor.
CYBER, simplified & explained
SECTION TWO
WHEN BUSINESS IS THRIVING — good cybersecurity will keep it that way! We want you to be aware of the risks, so you can keep chasing your passions. So what are you wondering?
-

Should my small business have a “security team?”
Definitely! But the team might be you, at first. While all cybersecurity teams are different, they all include leaders, experts, and partners. Learn to build one that keeps your company safe.
-

How should I control access to my computer systems?
We recommend you take a zero trust approach. Zero trust is when you deny everyone access to your computer systems until they’re properly verified. Learn how to keep the bad actors out!
-

So if I have a good firewall, I'm a modern day Fort Knox, right?
Haha…ahhh…no. But you are on the right path to defense in depth! Defense in depth is when you defend against cyber threats with multiple levels of protection. Don’t get scared by jargon. Learn the basics today!
-

How much security training does my team need?
Enough to help them help you! Cybersecurity awareness training is critical for business because it educates employees on the best tactics for keeping your company safe from cyber threats.
-

If I am in the “cloud,” I am protected, right?
Yes and no. Yes, since most cloud providers will HELP secure your cloud environment (to a point). And no, you still have to account for those assets and track them. You must stay on top of all your internet-facing assets now and until time ends. Learn more about how today!
-

So if I am new to all this, where should I start?
Don’t worry. We have you covered! It all begins with a solid understanding of cybersecurity basics. We have crafted an entire section for those just starting in the cyber world. We aim to get you as much information as possible but not overwhelm you.
READY FOR MORE epic content?
SECTION THREE
SMASH THE BUTTON below to read all our articles for SMBs!
LET’S WORK TOGETHER ON
Content for you!
Do you want to use our content for your site or training material, or would you like us to write curated white-label content for you? We can help you!

"By failing to prepare, you are preparing to fail."
- Benjamin Franklin